Outline Procedures for Dealing With Different Types of Security Breaches
Security Procedures in a Salon. Procedure on dealing with an information security breach incident.
6 Steps To Developing A Data Breach Response Plan Spectral
Stock control procedures could be tightened to lesson any opportunities.

. My question was to detail the procedure for dealing with the following security breaches 1loss of stock 2loss of personal belongings 3intruder in office 4loss of client. Security breaches can be caused by the theft of a laptop computer or electronic device a hacker who gains access to confidential records or. Salons are included in this statistic and may be at.
Procedures involving the locking away of valuable items could be introduced to lessen the opportunity of theft. Deal with the personal data breach 3515. You must have plans in place to respond effectively to health and safety incidents and other emergencies that might occur at an event.
Just as important as these potential financial and legal liabilities is. P8 outline procedures for dealing with different types of security breaches M6 review the effectiveness of procedures for dealing with different types of security breaches. Data breaches can be avoided if mitigating steps are taken early on such as when an event or incident occurs.
A breach of this procedure is a breach of Information Policy. Data breaches can be viewed. After the owner is notified you must inventory equipment and records and take.
What causes a security breach to occur. The first step when dealing with a security breach in a salon would be to notify. The measures taken to mitigate any possible adverse effects.
Outline procedures for dealing with different types. Dealing with a security breach is difficult enough in terms of the potential fiscal and legal consequences. The first step when dealing with a security breach in a salon would be to notify the salon owner.
Information assets - our data files and documents in any format paper. Different Types of Data Breaches. Ad Award-winning cybersecurity documentation - editable policies standards and controls.
Procedures for dealing with security breaches should focus on prevention although it is also important to develop strategies for addressing security breaches in process. What are the procedures for dealing with different types of security breaches within a salon. Breaches will be.
This sort of security breach. Some key terms that are used in this procedure are. Businesses lose billions of dollars annually and may even fail due to losses related to crime.
A security breach occurs when an intruder employee or outsider gets past an organizations security measures and policies to access the data.
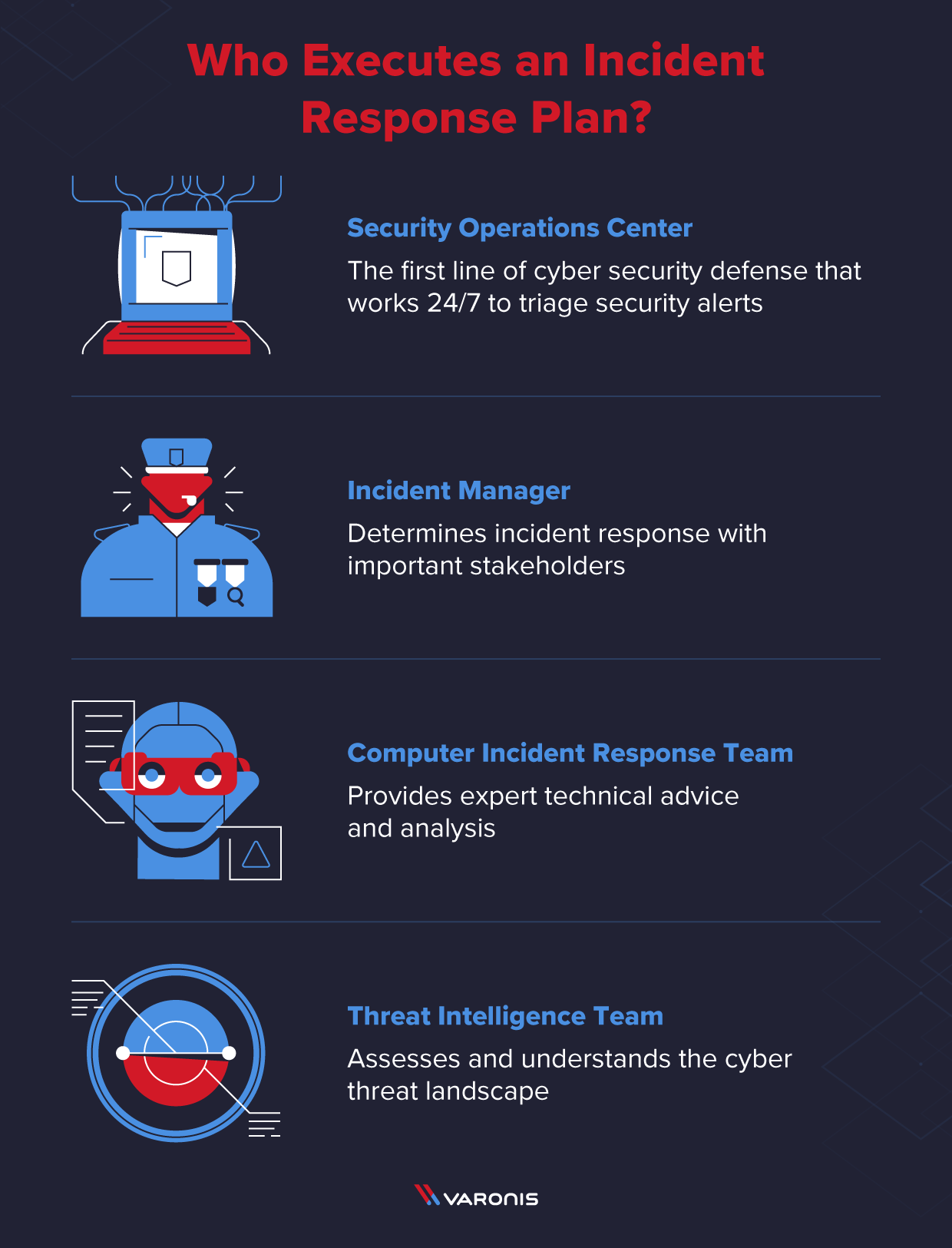
What Is An Incident Response Plan And How To Create One

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
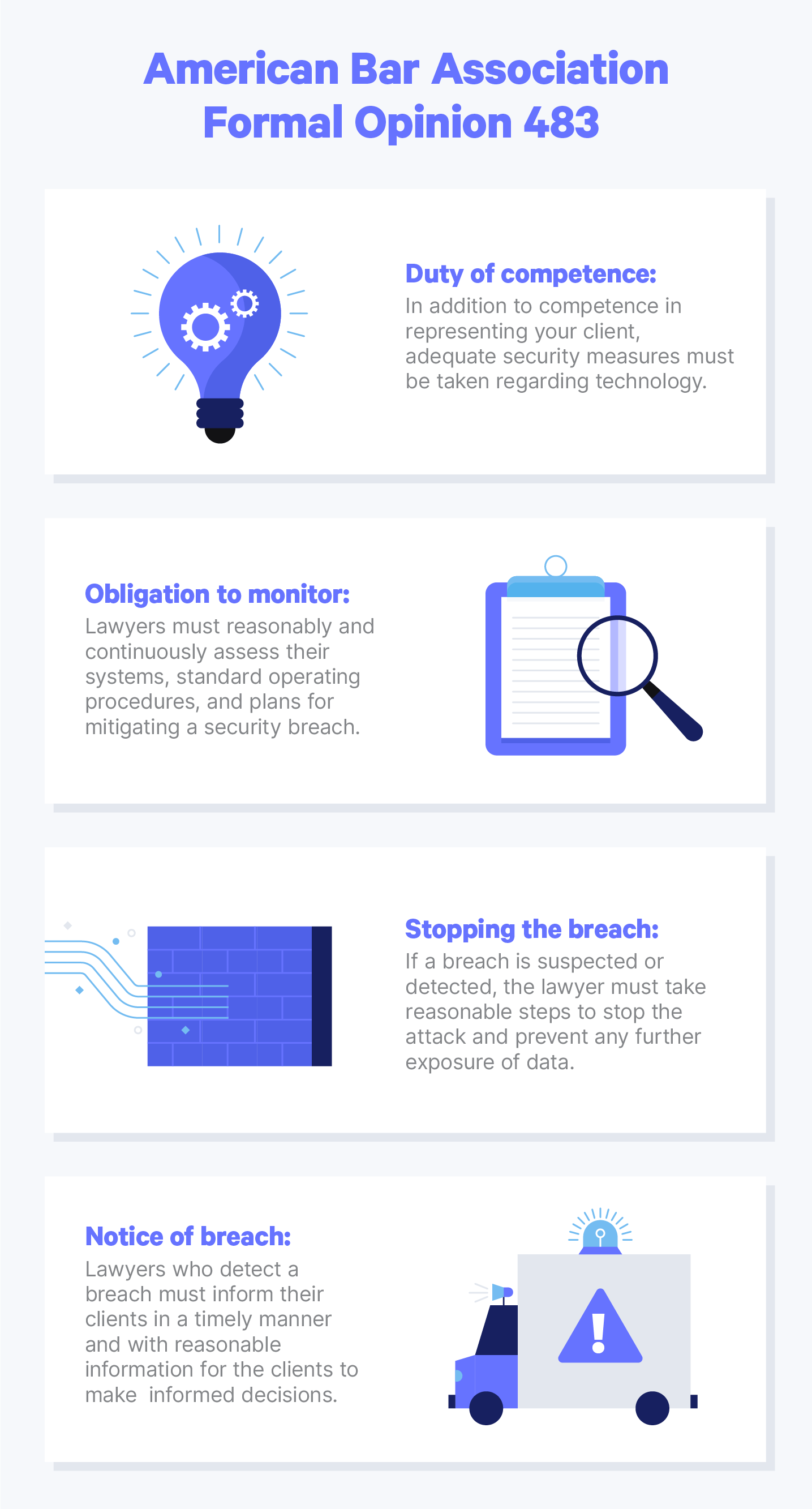
A Guide To Data Security For Law Firms Embroker

Data Breach Procedure Style Hair Beauty

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System
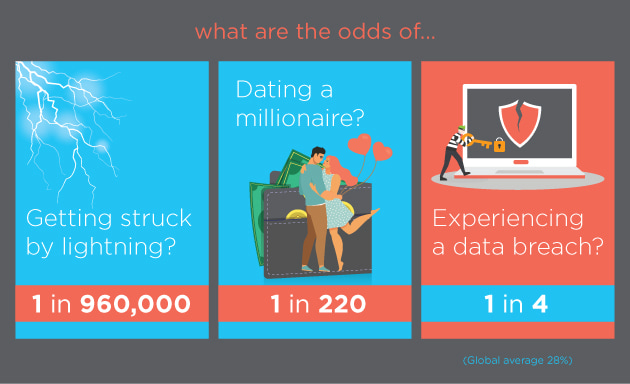
6 Steps To Developing A Data Breach Response Plan Spectral
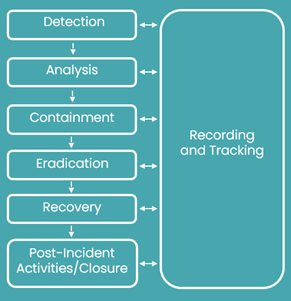
Incident Response Policy And Procedure Icims

1 Information Security Compliance System Owner Training Module 3 Risk Analysis And Security Plan Richard Gadsden Information Security Office Office Of Ppt Download

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
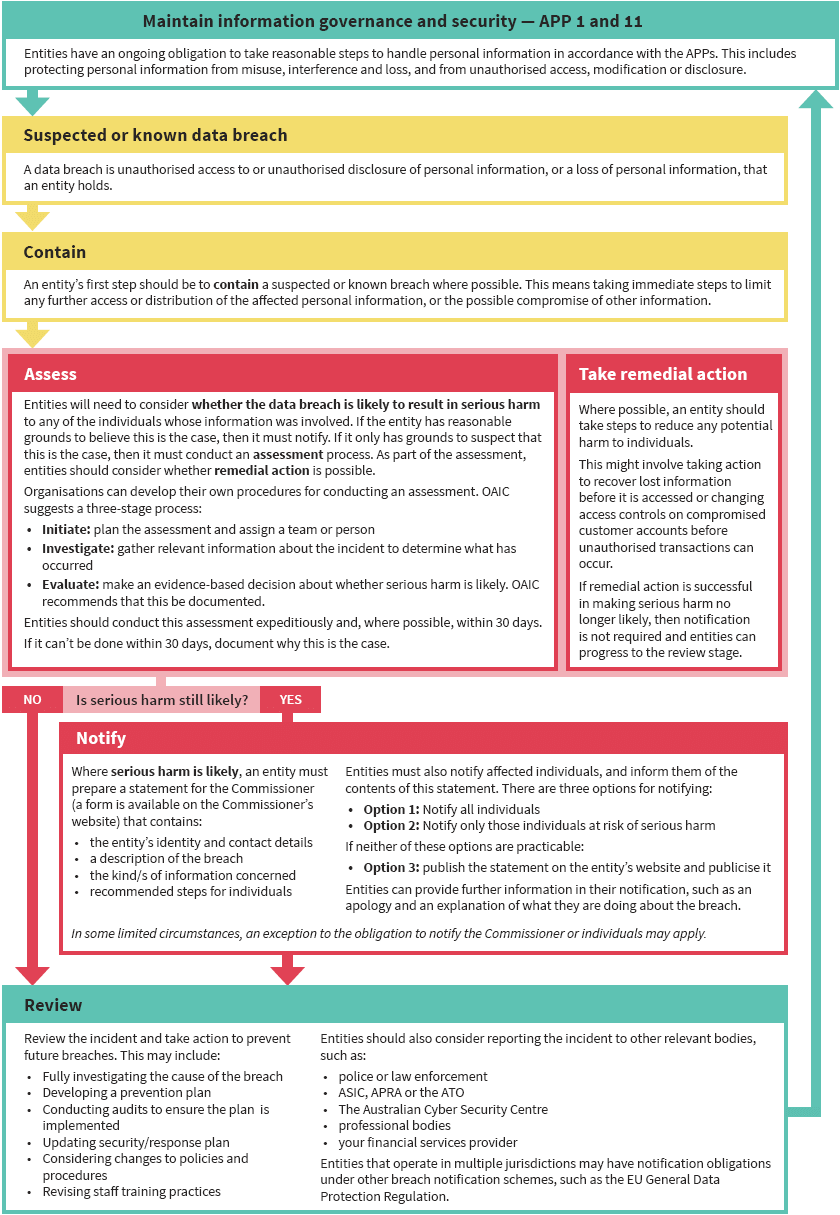
Part 3 Responding To Data Breaches Four Key Steps Home

6 Steps To Developing A Data Breach Response Plan Spectral

Security Policies And Procedures Ppt Download

6 Steps To Developing A Data Breach Response Plan Spectral

Unit 2 D1 Blended Learning Pages 1 2 Flip Pdf Download Fliphtml5

Security Breaches What You Need To Know
Data Breach Response Plan Home

7 Key Steps To Investigate A Data Breach With Checklist Ekran System


Comments
Post a Comment